-
Which option is the AWS customer responsible for under the AWS shared responsibility model? (Select two.)
-
✓ *Security group configuration
-
❏ Physical servers
-
✓ Client-side data
-
❏ Edge location infrastructure
-
❏ Availability Zone security
-
-
Which AWS IAM resource explicitly grants or denies permissions to a user or group of users?
-
❏ IAM roles
-
❏ IAM users
-
❏ IAM groups
-
✓ IAM polices
-
-
What is the correct term for the process of verifying a user’s identity as a developer?
-
❏ Endorsement
-
✓ Authentication
-
❏ Confirmation
-
❏ Authorization
-
-
Which statements about IAM user authentication are true? (Select two.)
-
✓ AWS credentials to authenticate with any supported services must be provided.
-
✓ A user name and password to authenticate to the console must be provided.
-
❏ A .pem or .ppk file is used to authenticate programmatically to the AWS API.
-
❏ It is a best practice to use the account root user credentials to authenticate programmatically by using the AWS CLI.
-
❏ Each AWS account can have only one administrator who manages other IAM users.
-
-
Which suggestion is in AWS recommendation for securing AWS credentials for applications that run on EC2 instances?
-
❏ Enable AWS credentials in the software SDK client code
-
❏ Store credentials in local AWS configuration files.
-
✓ Create an AWS IAM role and attach it to the EC2 instance.
-
❏ Create an AWS IAM user and attach it to the EC2 instance.
-
-
What is the format of IAM policies that defies below API calls an entry can invoke?
-
❏ YAML
-
❏ SAML
-
❏ CSV
-
✓ JSON
-
-
An administrator created an AWS IAM group called managers within an AWS account. A _ policy is attached to the manager’s group. It allows managers to read from and write to an S3 bucket in the same AWS account. What is this type of policy?
-
✓ Identity-based
-
❏ Resource-based
-
❏ Cross-account access
-
❏ AdministratorAccess managed
-
-
Which statement reflects best practices when granting permissions to users, groups, roles, and resources?
-
❏ Create policies that allow broad access and then limit permissions as needed, based on usage.
-
❏ Use the account root user for routine tasks that the administrator performs.
-
✓ Create policies that follow the principle of least privilege.
-
❏ Do not set policies for individual resources.
-
-
What is the effect of the following policy statement?
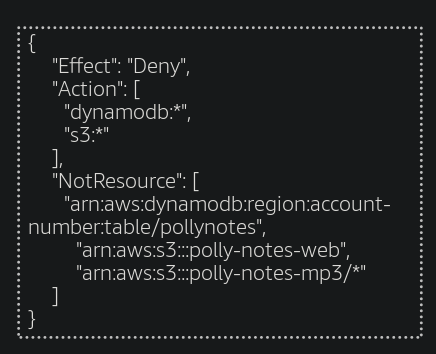
-
✓ Denies action on DynamoDB or Amazon S3 resources except for the resources that are listed in the NotResources element.
-
❏ Denies action on the DynamoDB table or S3 buckets that are listed in the NotResources element.
-
❏ Denies the ability to write to the policy notes DynamoDB table.
-
❏ Denies the ability to read from the policy-notes-web S3 bucket.
-
-
Which statements are true about evaluation logic for AWS IAM policies? (Select two.)
-
❏ You cannot have deny and allow statements in the same policy.
-
❏ An explicit allow overrides an explicit deny.
-
✓ An explicit deny overrides an explicit allow.
-
✓ By default, all requests are denied.
-
❏ By default, all requests are allowed.
-